

In the digital age, cyberattacks are becoming more frequent, unpredictable, and devastating. The estimated cost of cybercrime in the cybersecurity market is projected to increase by $6.4 trillion (+69.41%) from 2024 to 2029. By 2029, it is expected to reach a record $15.63 trillion after eleven consecutive years of growth.
Organizations face the challenge of defending against ever-evolving threats, where the speed of detection and response can mean the difference between a near-miss and a catastrophic breach.
Imagine having a security team that's always alert, powered by an intelligent, tireless assistant that never sleeps, analyzing vast amounts of data, and making real-time decisions. This is the promise of automated incident response.
Automated incident response is more than a buzzword; it’s the backbone of modern cybersecurity, offering unparalleled speed, efficiency, and precision. By automating routine tasks and using advanced analytics, automated incident response ensures that threats are swiftly identified and neutralized before they can cause significant harm.
In this article, we will explore how automated incident response works, its core benefits, and why it is a game-changer for organizations seeking to stay ahead in the battle against cybercrime.
Let’s begin by understanding an automated incident response.
Automated incident response refers to the process of using advanced technologies such as Artificial Intelligence (AI), Machine Learning (ML), and predefined rules to detect, analyze, and respond to security incidents with minimal human intervention.
It plays a critical role in modern cybersecurity by automating repetitive tasks and ensuring faster, more accurate responses to potential threats. These systems analyze data from multiple sources, identify patterns, and execute predefined actions based on specific criteria.
Now that the definition is clear, let’s explore the importance of automated incident response.
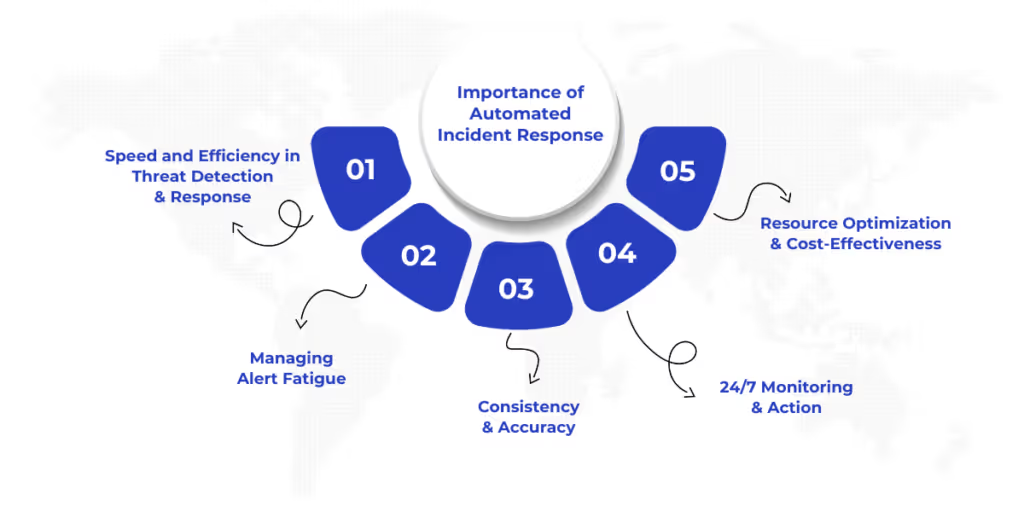
As cyber threats continue to evolve at an unprecedented pace, traditional manual methods of handling incidents are becoming obsolete. Security teams are overwhelmed, and attackers are more sophisticated than ever. This is why automated incident response is not just an advantage—it’s a necessity.
The first minutes of a security incident are crucial. Automated systems detect and respond to threats in real time, drastically reducing response times. By automating threat detection and correlating data from various sources, these systems identify suspicious activities, allowing security teams to act swiftly and minimize damage.
Security teams are constantly overwhelmed by alerts, many of which are false positives. This overload leads to alert fatigue, where real threats can be overlooked. Automated systems intelligently filter and prioritize alerts, allowing teams to focus on the most critical incidents, which significantly enhances operational efficiency.
Human decision-making during security incidents can be influenced by stress and workload, leading to potential errors. Automated systems, however, follow predefined rules to execute responses consistently and accurately. This ensures that every incident is handled according to best practices, eliminating the variability introduced by human error.
Cyber threats don’t follow business hours, and neither do automated systems. These tools provide continuous monitoring, scanning networks, and endpoints for suspicious activity around the clock. This constant vigilance helps detect and mitigate threats that may go unnoticed by human teams during off-hours.
Security teams are often under-resourced, dealing with high volumes of incidents and limited staff. Automating incident response reduces manual workloads, freeing up professionals to focus on more complex tasks, such as threat hunting and investigations. Automation also helps reduce costs by decreasing the need for additional staff while increasing the overall efficiency of the security operation.
After understanding why automated incident response is crucial, let’s delve into the core benefits it offers.
Also Read: Automated Incident Triage in Cybersecurity: Role and Use Cases
Here are the core benefits of automated incident response:
Automated systems significantly reduce Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). By quickly detecting potential threats, automation accelerates response times, minimizing the risk of further damage.
Automated incident response reduces alert fatigue by filtering out irrelevant alerts and prioritizing genuine threats. This enables security teams to maintain focus on critical issues and avoid burnout.
By automating time-consuming tasks, security teams can allocate more time to strategic decision-making and complex threat management, enhancing overall productivity.
Automated systems ensure consistent execution of incident response actions, eliminating the risk of human error. This consistency strengthens the organization’s security posture, as each incident is handled according to established protocols.
Automated incident response reduces the need for constant human oversight, allowing organizations to allocate resources more efficiently. By handling routine tasks, automation helps reduce operational costs while maintaining strong defense capabilities.
With these benefits in mind, let’s explore how automated incident response systems work in practice.
Automated incident response systems rely on several processes to function effectively:
These systems collect data from various sources, such as logs, network traffic, and endpoint activity. Advanced analytics are then used to identify patterns that might indicate a potential security incident.
AI adoption for incident response increased by 21%, with 63% of organizations already using it and 34% planning to implement it. Once data is analyzed, ML and AI algorithms help prioritize alerts based on their severity. These technologies also identify patterns in attack Tactics, Techniques, and Procedures (TTPs), improving future detection.
Automated response systems come with predefined playbooks that outline specific steps to take when a particular type of incident is detected. These playbooks execute actions such as blocking an IP address, quarantining a file, or notifying relevant team members.
In the next section, let’s have a look at key tasks in incident response automation.
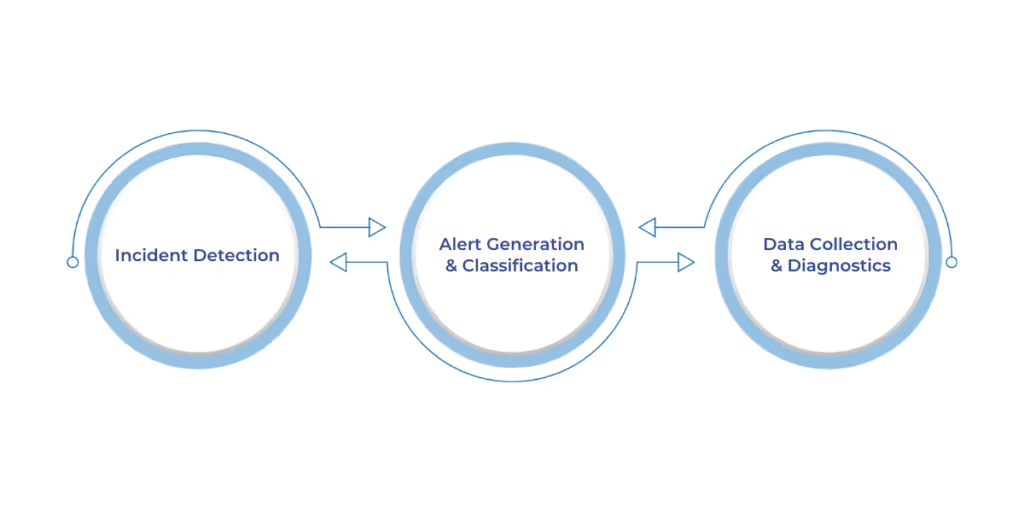
Automated systems perform several essential tasks to ensure timely and effective threat mitigation:
To maximize the effectiveness of automation, selecting the right tools is essential.
Also Read: DevOps Incident Management Strategies and Processes
Choosing the appropriate automated tools is vital for an efficient security operation. Here are key factors to consider:
Having the right tools in place enables organizations to leverage automation across various use cases.
Automated incident response tools are applied in various ways, including:
Despite these advantages, automation also comes with challenges that organizations must address.
Despite its advantages, automated incident response presents several challenges:
To overcome these challenges, organizations should follow best practices.
To ensure automated systems are effective, organizations should:
Automated incident response is an essential component of modern cybersecurity. With the increasing complexity of cyber threats, organizations must embrace automation tools to respond to incidents swiftly and efficiently.
Automation reduces response times, minimizes alert fatigue, and improves overall productivity. However, organizations must remain mindful of potential challenges and adopt best practices to ensure the system’s effectiveness.
In today’s cybersecurity landscape, automated incident response is no longer optional—it's essential for organizations to protect critical assets and respond to threats proactively.
Don’t let cyber threats compromise your business. With automated incident response, you can detect, analyze, and neutralize threats in real time—without the burden of manual intervention.
WaferWire offers cutting-edge security automation solutions that reduce alert fatigue, improve response times, and fortify your defenses.
Take proactive control of your security today. Explore WaferWire’s automated incident response solutions now!

