
Automated Incident Triage in Cybersecurity: Role and Use Cases
Murthy S
2025-03-11

Talk to our cloud experts
Subject tags
Cyber threats don’t knock before entering—they break in, lurk, and strike when least expected. Security teams face an overwhelming flood of alerts daily, struggling to separate real threats from false positives. The challenge isn’t just about volume; it’s the speed, complexity, and limits of human-driven threat detection.
Automated incident triage is transforming this situation. It filters out the noise by employing AI-driven precision to detect, analyze, and prioritize threats in real time. This enables security teams to concentrate on what genuinely matters—stopping actual attacks before they escalate.
So, what’s holding traditional incident response back, and how can automation give security teams an edge? In this article, we’ll explore why manual methods struggle to keep up, how AI-powered triage reshapes cybersecurity, and how real-world use cases prove its impact.
Automated Incident Triage in Cybersecurity
Cybersecurity teams face a constant battle against an overwhelming number of security alerts. Every day, thousands of potential threats flood security systems. However, only a small fraction require immediate attention. Sorting through this noise is time-consuming, costly, and often ineffective.
Instead of relying on manual review, organizations are turning to automation to filter, analyze, and prioritize security incidents faster and more accurately. This approach helps security teams focus on real threats rather than wasting time on false alarms. Businesses can strengthen their defenses by reducing manual effort and improving response times without overburdening their analysts.
For industries like retail, manufacturing, financial services, and utilities, where cyber risks can lead to compliance issues, economic losses, and operational disruptions, automation is no longer optional—it’s critical to maintaining a strong security posture.
Automation Transforms Cyber Incident Management
Instead of relying solely on human analysts to process alerts, businesses are integrating automated incident triage to improve detection speed and accuracy. AI-powered triage doesn’t replace security teams but acts as a force multiplier, ensuring that:
- High-risk alerts are immediately prioritized and escalated for human review
- False positives are filtered out, reducing unnecessary investigations
- Incident correlation helps detect complex attack patterns, improving early threat identification
The Impact of Automated Triage on Security Operations
- Faster Response Times: IBM's AI-powered Threat Detection and Response Services can automatically escalate or close up to 85% of alerts, accelerating security response timelines.
- Lower Operational Costs: Organizations extensively using security AI and automation in their prevention workflows incurred an average of $2.2 million less in breach costs compared to those without such technologies.
- More Accurate Threat Detection: AI-enhanced models have reduced network traffic analysis time by 50% and improved anomaly identification performance by 30%, leading to more efficient incident response.
Automated Triage in Threat Sorting
Not all security threats require immediate action. A phishing attempt and an active ransomware attack demand different response strategies. Automated triage involves sorting incidents based on risk severity and business impact.
How Automated Triage Assigns Priorities
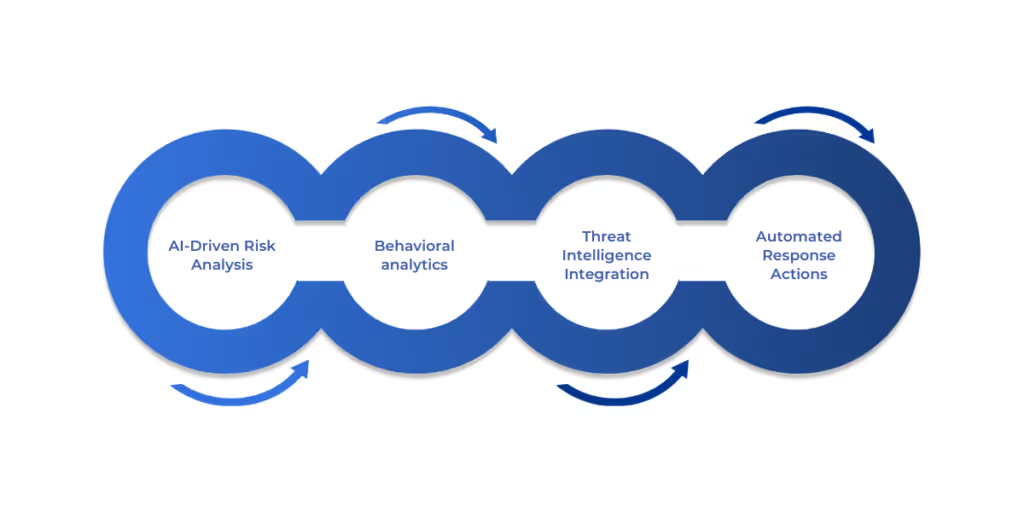
- AI-Driven Risk Analysis: Machine learning identifies attack patterns and assigns risk scores.
- Behavioral analytics: Unusual login attempts, API anomalies, and suspicious network traffic are flagged.
- Threat Intelligence Integration: Matches indicators of compromise (IoCs) with real-time threat databases.
- Automated Response Actions: High-risk threats trigger immediate containment measures (e.g., blocking an IP or isolating a compromised endpoint).
Understanding how automated incident triage assigns priorities is crucial, but it's equally important to delve into the mechanics behind this process.
How Automated Incident Triage Works
Modern cybersecurity environments generate massive amounts of security data from various monitoring tools, firewalls, intrusion detection systems, and cloud platforms. Automated incident triage processes this information in real time, correlating alerts, filtering noise, and prioritizing incidents based on predefined rules and AI-driven risk assessments.
When a high-priority event is detected, the system can automatically trigger response actions, such as notifying security teams, creating a response ticket, or isolating a compromised endpoint. This reduces manual effort, speeds up incident resolution, and ensures that only critical threats demand human attention.
Key Components of an Automated Incident Triage System
Each stage in automated incident triage is crucial to ensuring that security teams can detect, analyze, and respond to threats efficiently. Here’s how the system works, step by step.
Data Collection & Ingestion
Security data is pulled from multiple sources, including:
- Network firewalls and intrusion detection systems (IDS/IPS)
- Cloud security logs from environments like AWS, Azure, and Google Cloud
- Application logs and endpoint detection tools
- Threat intelligence feeds to cross-check attack patterns
Alert Correlation & Noise Reduction
Not every alert is a real threat. Automated triage systems filter out false positives by:
✔ Grouping related alerts that originate from the same source
✔ Ignoring low-priority events that do not match threat patterns
✔ Detecting recurring attack behaviors to differentiate true threats from system anomalies
Incident Classification & Prioritization
Once alerts are processed, the system categorizes incidents based on severity, impact, and urgency:
✔ High-Priority Incidents: Active security breaches, malware detections, and unauthorized access attempts trigger immediate action.
✔ Medium-Priority Incidents: Suspicious activities that require further analysis before action is taken.
✔ Low-Priority Incidents: Logged for reference but do not require immediate intervention.
Automated Workflow Execution
For high-risk threats, predefined workflows trigger immediate response actions:
✔ Creating incident tickets for security analysts to investigate.
✔ Notifying IT and security teams about an ongoing attack.
✔ Executing predefined security measures like blocking an IP address or enforcing multi-factor authentication (MFA) for flagged accounts.
Incident Response & Remediation
Once an incident is classified and escalated, response teams analyze the root cause and take corrective actions, such as:
✔ Quarantining infected endpoints to stop malware spread.
✔ Patching vulnerabilities that were exploited during an attack.
✔ Restoring affected systems while preserving forensic evidence.
Post-Incident Review & Reporting
After the incident is resolved, the system archives key data for analysis:
✔ Performance metrics: Response time, detection accuracy, and resolution efficiency.
✔ Threat intelligence updates: Learning from past incidents to improve future threat detection.
✔ Compliance tracking: Ensuring regulatory requirements (e.g., GDPR, PCI-DSS) are met.
Now that we’ve explored how automated incident triage functions, let’s break down the key processes that drive its efficiency and ensure real-time security enforcement.
Processes in Automated Incident Triage
Security teams face constant alerts, but not all incidents require immediate action. Without automation, sorting through these notifications can take hours—or even days—leaving organizations vulnerable to real threats. Here’s how it works:
Key Processes in Automated Incident Triage:
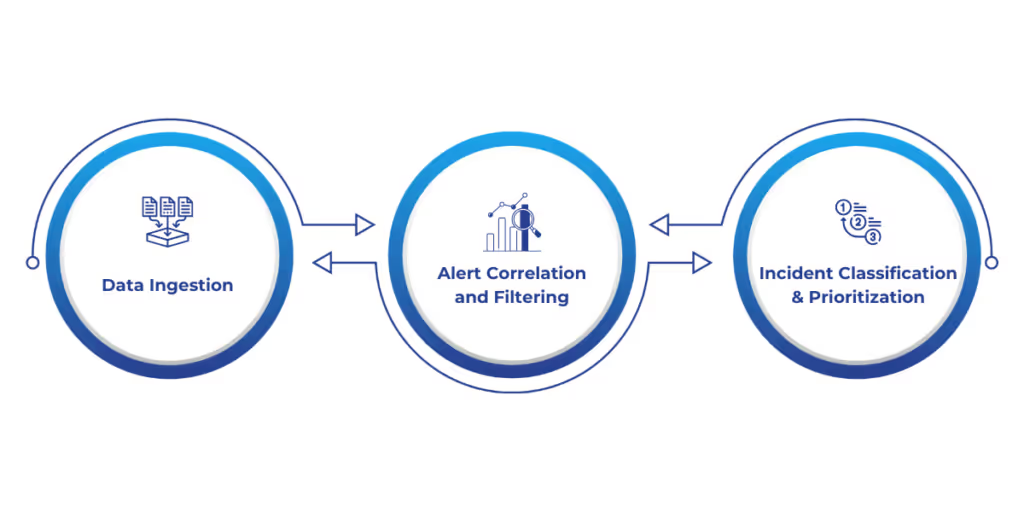
Data Ingestion: The system gathers and compiles information from various sources, such as firewalls, intrusion prevention systems (IPS), application logs, and other monitoring tools. This thorough data collection guarantees that no possible danger vector is missed.
Alert Correlation and Filtering: Once data is ingested, the system analyzes and correlates alerts in real time. By grouping related alerts and filtering out noise, such as false positives, the system ensures that only pertinent alerts are escalated for further analysis.
Incident Classification and Prioritization: The system classifies incidents based on severity and potential impact, using predefined rules and AI models. High-priority incidents trigger immediate response actions, such as notifying stakeholders, creating incident tickets, or executing predefined remediation steps.
Classifying and prioritizing incidents is just one step. Next, we will examine how alerts are managed and how security teams ensure rapid response to real threats.
Alert Management
Effective alert management is key to solid cybersecurity. A strong system ensures real threats are spotted quickly and reduces the risk of missing critical issues.
To refine your alert management, focusing on normalization and deduplication is important. By grouping alerts into logical sets, you simplify the analysis, making it easier to spot patterns and trends. Additionally, prioritizing alerts based on their impact on business operations ensures that your team responds to the most urgent threats first. Let's explore the key elements of a structured alert management process to improve your response time and accuracy.
Normalization and Deduplication
Security alerts come from multiple sources, including firewalls, intrusion prevention systems (IPS), endpoint detection platforms, and cloud security tools. Each system generates logs in different formats, making it difficult for security teams to analyze and correlate events efficiently.
What is Normalization?
Normalization is the process of converting alerts into a uniform format, ensuring that security systems and analysts can easily compare them.
Example:
One system might log an unauthorized login attempt as “Access Denied," while another labels it “Failed Login". Normalization standardizes these terms to ensure consistent categorization across security platforms.
Why It Matters: Without normalization, security teams might misinterpret alerts, leading to missed threats or incorrect prioritization.
What is Deduplication?
Duplicate alerts overwhelm security teams, often causing alert fatigue, where analysts become desensitized to notifications. Deduplication removes repeated alerts from the same event, ensuring that security teams focus only on unique threats. For example, if multiple security tools detect a single malware attack, deduplication consolidates all the alerts into one actionable incident instead of sending multiple notifications.
How Security Tools Use Deduplication:
✔ AppSOC aggregates alerts from multiple sources, reducing redundancy and improving visibility.
✔ Jira Service Management eliminates duplicates by analyzing alert attributes like source, timestamp, and content before escalation.
Correlation of Alerts
Alerts rarely happen in isolation—cyberattacks often trigger multiple security events across different systems.
How Correlation Works:
- Grouping Related Alerts: If multiple login failures occur from a single IP followed by a privileged access attempt, correlation links these events to detect a possible brute-force attack.
- Identifying Coordinated Attacks: Correlation matches new alerts against past attack patterns, helping analysts detect multi-stage threats.
- Automated Alert Merging: Instead of creating separate cases for every login attempt, firewall block, and suspicious API request, correlation merges them into a single, meaningful security incident.
Assigning Priority: Separating Critical Threats
Not every alert deserves immediate attention. Prioritization ensures that security teams respond to critical incidents first while logging lower-risk alerts for later review.
How Prioritization Works:
- Severity Analysis: Determines if the alert involves a major security threat or a minor system issue.
- Business Impact Evaluation: Focuses on threats that could compromise sensitive data, disrupt services, or cause financial loss.
- Threat Intelligence Matching: Uses databases of known attack patterns to identify whether the alert matches an ongoing cyberattack.
The next section explores how automation strengthens incident triage, making response times even faster.
Benefits of Automation in Cybersecurity Incident Triage
By leveraging automation, businesses can detect threats faster, reduce response times, and improve overall security efficiency.
Here’s how automation drives real impact:
Faster Recovery with Reduced MTTR
Every second counts when responding to security incidents. A delay of even minutes can allow attackers to move deeper into a system, causing financial and operational damage. Automated incident triage drastically reduces Mean Time to Recovery (MTTR) by:
- Detecting security incidents in real time, eliminating delays caused by manual reviews.
- Automatically containing high-risk threats by isolating affected systems before the attack spreads.
- Triggering predefined response actions, such as blocking malicious IPs or revoking compromised user access.
Increased Efficiency
Security teams spend up to 60% of their time dealing with false positives and low-priority alerts. This not only drains resources but also delays responses to critical threats. Automation improves efficiency by:
- Filtering out irrelevant alerts, allowing analysts to focus on verified threats.
- Automating routine investigation tasks, such as checking threat intelligence databases and scanning for malicious activity.
- Reducing analyst fatigue, preventing burnout, and improving threat response quality.
Unified Incident Management for Better Visibility
Cybersecurity incidents originate from various sources: firewalls, endpoint monitoring, cloud security logs, and SIEM tools. In the absence of a unified system, security teams confront scattered alerts, complicating investigations difficult.
Automation enables:
- A centralized dashboard that consolidates all security alerts into a single, organized view.
- Automatic correlation of related incidents, preventing teams from treating interconnected events as isolated cases.
- Better coordination between security tools, ensuring faster, more comprehensive responses.
Automation speeds up threat detection, but AI and machine learning take it a step further. Next, we’ll explore how AI enhances incident triage with intelligent classification, tagging, and real-time decision-making.
Utilizing AI and Machine Learning in Incident Triage
AI and machine learning are transforming incident triage. These technologies boost security and cut down on manual tasks. AI-driven systems learn and adapt as threats evolve. Generative AI helps with incident classification and status updates. AI also dynamically generates tags and explains classifications.
Generative AI's Role
- Classification and Updates: Generative AI categorizes incidents and provides real-time status updates. AI analyzes alerts, assesses content, and determines if the alert indicates malicious activity, enhancing threat detection.
- Dynamic Tag Generation: AI automatically generates tags and classification explanations. This ensures every alert is thoroughly triaged, and AI consistently investigates incidents.
AI-Powered Automation
- Triage Automation: AI automates the triage process by categorizing incidents based on severity. Machine learning algorithms correlate multiple data points to provide context and reduce false positives.
- Workload Reduction: AI-enabled incident triage significantly reduces the workload on security analysts, allowing them to focus on complex tasks3. AI ensures no potential threat is overlooked.
- Adaptive Strategies: AI systems continuously learn and adapt to new attack methods, ensuring a proactive cybersecurity posture. AI algorithms are particularly effective in automating incident triage, swiftly prioritizing threats by assessing their severity, urgency, and potential impact with exceptional accuracy.
Conclusion
Cyber threats aren’t slowing down, and manual security operations can’t keep up. Automated incident triage isn’t just an upgrade—it’s the backbone of a modern, resilient cybersecurity strategy. The ability to detect, classify, and respond to threats in real time is a business necessity.
But automation alone is not enough. Organizations need the right expertise, the right technology, and the right execution. That’s where WaferWire comes in.
Why Leading Enterprises Trust WaferWire?
WaferWire isn’t just another security vendor. We are a strategic partner for enterprises and mid-market companies looking to strengthen their security posture. Our deep expertise in security automation, AI-driven incident response, and Microsoft’s security ecosystem enables us to help businesses in:
- Eliminating alert fatigue with intelligent, automated incident triage solutions that filter and prioritize critical threats.
- Accelerating response times through AI-powered threat detection and containment, enabling faster identification and mitigation of security risks.
- Reducing operational risks by centralizing security management and integrating seamlessly with cloud environments, ensuring comprehensive oversight of your security infrastructure.
Are you ready to take cybersecurity to the next level? Connect with us today and discover how automated incident triage can revolutionize your security operations.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)












