
The Critical Role of DevSecOps in CI/CD Security
Murthy S
2025-02-13

Talk to our cloud experts
Subject tags
Security can’t be an afterthought in modern software delivery. DevSecOps CI/CD integrates security seamlessly into development and deployment, ensuring vulnerabilities are caught early and automatically (not at the last minute).
By embedding security checks into every code commit, build, and deployment, DevSecOps eliminates bottlenecks, enhances compliance, and prevents threats before they escalate. It transforms security from a standalone process into an automated, collaborative, and scalable part of CI/CD pipelines.
This article reveals how security into CI/CD through DevSecOps strengthens protection while keeping development fast and agile.
DevSecOps in CI/CD Security
Security can’t be a last-minute fix—it must be built into the software development process. DevSecOps in CI/CD security ensures that security is embedded from the start, reducing risks without slowing down deployment.
What is DevSecOps?
DevSecOps combines development, security, and operations into a continuous workflow. Instead of treating security as a separate step, it integrates protective measures into every phase of the software development lifecycle (SDLC). This means security checks happen alongside coding, testing, and deployment.
Why It Matters in SDLC
In traditional development, security testing occurs at the end of the process, often leading to delays, missed vulnerabilities, and costly fixes. With DevSecOps, security becomes proactive, ensuring issues are caught early before they reach production.
Early Security Integration: The Key to Safe CI/CD
In CI/CD, code is constantly being built, tested, and deployed. Without DevSecOps, security gaps can be exploited before teams even notice them. Embedding security early prevents breaches, ensures compliance, and keeps deployments smooth.
Now that we understand why DevSecOps in CI/CD security is essential, let's break down the key components of a secure DevSecOps pipeline.
Key Components of a DevSecOps Pipeline
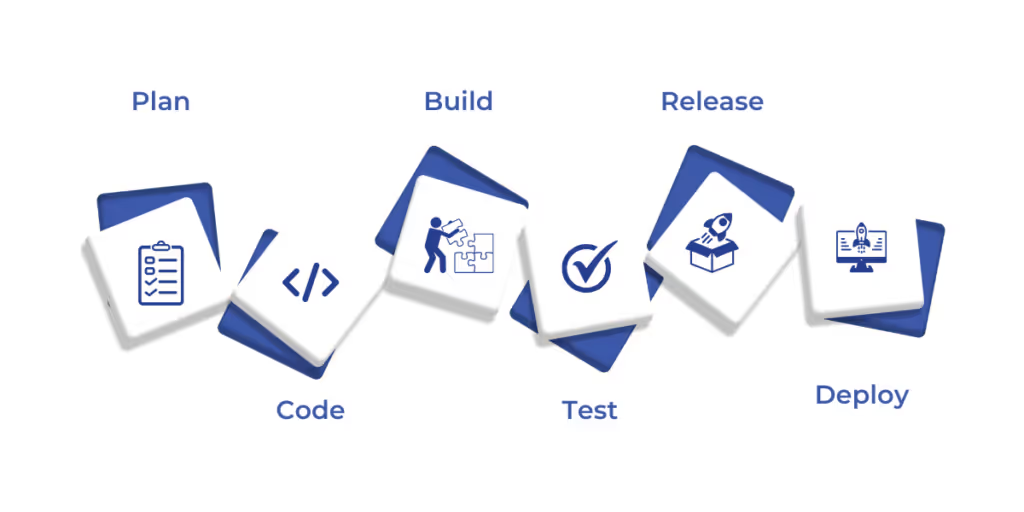
Security isn’t a separate process—it’s a built-in layer across development. With DevSecOps embedded in CI/CD pipelines, security becomes a constant presence at every stage, identifying and addressing vulnerabilities before they escalate. Here’s how it works:
- Plan: Security starts before a single line of code is written. During the planning phase, teams must identify risks, define security policies, and outline testing strategies.
- Code: Developers use linting tools, secret management, and automated scanning to prevent security flaws at the source. Storing sensitive data securely and following coding best practices reduces risk.
- Build: Static Application Security Testing (SAST) checks code for security flaws before deployment. It ensures vulnerabilities are caught during the build process, reducing the risk of security breaches.
- Test: Dynamic Application Security Testing (DAST) simulates real-world attacks on a running application to uncover security flaws.
- Release: Before pushing an update, vulnerability scans and penetration testing check for risks in infrastructure and third-party dependencies.
- Deploy: Security doesn’t end with deployment. Teams must ensure secure configurations, access controls, and runtime protections.
Now that security is embedded in each stage, let’s explore how to integrate these security measures seamlessly into CI/CD pipelines.
Integrating Security into CI/CD Pipelines
Every deployment carries risk, and a single unpatched vulnerability in an open-source component can expose an entire system.
Addressing Open-Source Vulnerabilities
Nearly 80% of modern applications use open-source components, but many come with undisclosed security risks. If left unchecked, a vulnerable third-party library could introduce security gaps.
- Automated dependency scanning tools, such as Snyk, Black Duck, and OWASP Dependency-Check, continuously monitor open-source libraries for security flaws.
- Integrating Software Composition Analysis (SCA) within CI/CD pipelines ensures known vulnerabilities (like CVEs) are flagged before deployment.
- Regular patching and version updates keep dependencies secure, reducing exposure to zero-day exploits.
Embedding Security in CI/CD Pipelines
Security must be integrated into every code commit and deployment cycle. If vulnerabilities are discovered after release, fixing them can cost up to 100 times more than if they were identified during development.
- Static Application Security Testing (SAST) tools scan source code for weaknesses before triggering builds.
- Dynamic Application Security Testing (DAST) mimics real-world attacks to identify application vulnerabilities.
- Infrastructure as Code (IaC) security tools, such as Checkov and Terraform Sentinel, ensure deployment environments are hardened before provisioning.
Automating Continuous Monitoring
Security doesn’t stop at deployment. Continuous monitoring detects misconfigurations, unauthorized access, and API abuse in real time.
- Runtime protection tools like Falco and Aqua Security track system behavior and trigger alerts for anomalies.
- Security Information and Event Management (SIEM) solutions, including Splunk and AWS GuardDuty, provide centralized threat intelligence and log analysis.
- Automated response mechanisms shut down compromised environments before attackers exploit weaknesses.
Even with strong security measures, challenges remain. Let’s examine common CI/CD security risks and how to solve them.
Common CI/CD Security Challenges and Solutions
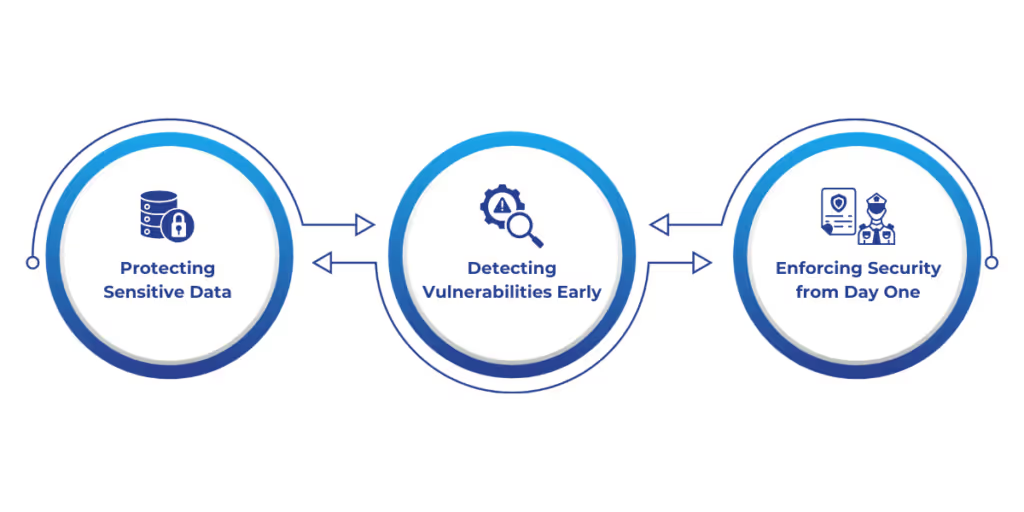
Security gaps in CI/CD pipelines expose businesses to data breaches, compliance violations, and operational disruptions. Many attacks stem from poor security hygiene, such as exposed credentials, unpatched dependencies, and misconfigured infrastructure. DevSecOps mitigates these risks by embedding security directly into development and deployment cycles.
1. Protecting Sensitive Data
Hardcoded secrets, exposed API keys, and misconfigured access controls are among the leading causes of security breaches. Attackers scan public and private repositories for embedded credentials, which can provide unauthorized access to databases, cloud services, and internal systems.
- Solution: Implement secrets management tools like AWS Secrets Manager, Azure Key Vault, or HashiCorp Vault to securely store and retrieve sensitive information.
- Best Practice: Before pushing code, use pre-commit hooks to scan for hardcoded credentials. Tools like TruffleHog and GitGuardian detect secrets in repositories before they become security liabilities.
- Additional Safeguard: Restrict access to secrets through role-based access control (RBAC) and enforce least privilege principles.
2. Detecting Vulnerabilities Early
If security issues are discovered late in the software lifecycle, they can become expensive and difficult to fix. Unpatched open-source dependencies, unvalidated inputs, and insecure configurations can create serious security flaws.
- Solution: Automate Software Composition Analysis (SCA) in CI/CD pipelines. Tools like Snyk, OWASP Dependency-Check, and Mend (formerly WhiteSource) continuously monitor third-party dependencies for known vulnerabilities and outdated versions.
- Best Practice: Apply automated patching for libraries with critical vulnerabilities. Set up CI/CD policies that fail builds if critical security risks are detected.
- Additional Safeguard: Use Static Application Security Testing (SAST) during development to catch code vulnerabilities before deployment. Dynamic Application Security Testing (DAST) can further validate security in a running environment.
3. Enforcing Security from Day One
Security isn’t just about scanning for risks—it must be actively enforced at every stage of development. Without CI/CD-level security controls, developers might bypass security best practices to speed up releases, increasing the risk of vulnerabilities slipping into production.
- Solution: Define security policies as code using tools like Open Policy Agent (OPA) and Checkov to enforce security standards automatically.
- Best Practice: Implement security gates in CI/CD pipelines that block deployments if security checks fail. This ensures compliance before the software is released.
- Additional Safeguard: Use IaC security tools to validate configurations before provisioning cloud environments. Misconfigured IAM roles, overly permissive network settings, and unencrypted storage are common attack vectors that IaC security tools can detect and prevent.
Next, we’ll explore essential tools for implementing DevSecOps and how they improve security without disrupting development workflows.
Tools and Technologies for Implementing DevSecOps
Security can become a bottleneck without the right technologies, delaying deployments and exposing businesses to risks.
Security Automation in CI/CD Pipelines
Manual security checks can’t keep up with fast development cycles. Automated security testing ensures vulnerabilities are caught before deployment.
- Jenkins and GitLab CI/CD enable seamless security integration by running security tests at every build.
- SonarQube performs Static Application Security Testing (SAST) to detect vulnerabilities in source code.
- OWASP ZAP automates Dynamic Application Security Testing (DAST) to identify runtime security flaws.
Outcome: Automated security testing reduces human error, speeds up risk detection, and ensures code security before production.
Container Security and Infrastructure as Code (IaC) Protection
Modern deployments rely on containers and infrastructure automation, but misconfigurations introduce security gaps.
- Aqua Security and Falco continuously monitor container workloads for suspicious activity.
- Terraform Sentinel and Checkov enforce IaC security policies, preventing misconfigured cloud infrastructure.
- AWS Inspector scans cloud workloads for vulnerabilities before deployment.
Outcome: Securing containers and infrastructure code ensures consistent, hardened environments, reducing security risks at scale.
Role of Automation in Security Governance
Security isn’t solely about identifying vulnerabilities; it’s also about upholding security standards automatically.
- An Open Policy Agent (OPA) enforces policy-as-code, blocking insecure configurations in CI/CD pipelines.
- Secrets management tools like AWS Secrets Manager prevent credential leaks in repositories.
- Security Information and Event Management (SIEM) tools, like Splunk, provide real-time security insights.
Outcome: Security automation reduces compliance risks, prevents policy violations, and strengthens incident response.
The right tools lay the foundation for a secure CI/CD pipeline, but best practices drive real results. Next, we’ll explore proven strategies to enhance CI/CD security with DevSecOps.
Best Practices for Strengthening CI/CD Security with DevSecOps
While automation plays a crucial role, success lies in how teams work together, how security is enforced, and how issues are detected before they escalate.
Security as a Shared Responsibility
One of the biggest mistakes in traditional security models is treating security as an isolated process. Developers push code, security teams audit it, and operations deploy it which often leading to conflicts, delays, and last-minute vulnerability fixes. This outdated approach doesn’t work in fast-moving CI/CD pipelines.
A successful DevSecOps CI/CD strategy demands collaboration from the start. Developers must understand secure coding practices. Security teams need to move beyond gatekeeping and work alongside developers to integrate security tools without slowing down innovation. Leadership must drive this shift, ensuring that security is a priority, not an afterthought.
Automating Security Without Disrupting Speed
Speed and security are often seen as competing forces in CI/CD. But security doesn’t have to slow down releases—it can accelerate them when done right.
- Instead of manual security approvals that create bottlenecks, use automated security checks within the pipeline.
- Code scanning tools (SAST) catch vulnerabilities before they reach production, ensuring that insecure code is fixed early.
- Dynamic security testing (DAST) simulates attacks in real time, helping teams fix security gaps before users are exposed.
By embedding security into the CI/CD workflow, businesses can ship faster with confidence, knowing that every release is secure by design.
Continuous Monitoring for Immediate Risk Detection
Threats don’t stop when an application goes live. Security must be ongoing, not a one-time checklist before deployment.
Real-time security monitoring ensures that teams are alerted immediately if an API is misconfigured, a vulnerability is exploited, or an unauthorized login attempt occurs. SIEM tools, security analytics, and threat detection platforms provide real-time insights that allow teams to react before damage is done.
For organizations handling sensitive data, regulatory compliance isn’t just a checkbox; it’s mandatory. Continuous security validation ensures that every release meets compliance requirements, protecting both customers and the business from breaches and legal consequences.
Conclusion
Fast releases mean nothing if security is compromised. A single vulnerability can wipe out trust, disrupt operations, and cost millions. However, security is more than just preventing breaches; it is also about instilling trust in each deployment. When security is baked into development, teams move faster, compliance becomes effortless, and risks shrink before they become problems.
Yet, implementing DevSecOps isn’t just about plugging in tools. It’s about changing how teams think, work, and collaborate. Security can’t be a last-minute checklist, it has to be part of the code, the pipeline, and the culture.
That’s where WaferWire comes in. We don’t just help businesses add security to their CI/CD pipelines; we make it a seamless part of the development process. Whether you’re in finance, retail, manufacturing, or utilities, we help you build, deploy, and scale securely without slowing down innovation. Talk to our expert today and take control of your security.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)












