

Incident response tools are critical in cybersecurity, which allows organizations to detect, analyze, respond, and recover from security incidents. These tools are designed to streamline the process of managing security events, helping security teams to identify threats quickly and mitigate risks before they escalate. As cyber threats become more sophisticated, the importance of having robust incident response tools cannot be overstated.
By using these tools, organizations can improve their ability to defend against attacks, minimize damage, and ensure business continuity. This article explores various types of incident response tools and how they contribute to a more secure infrastructure.
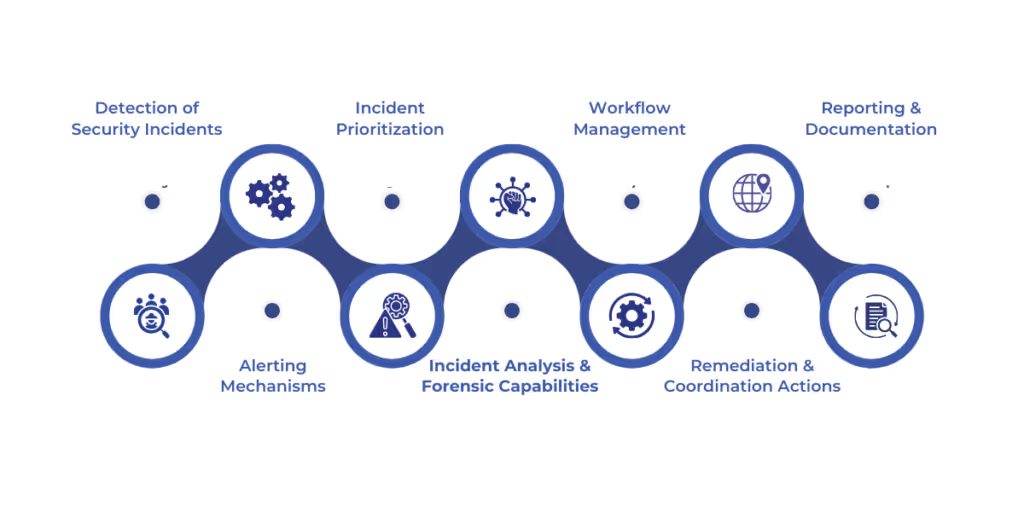
Incident response tools offer a variety of features designed to manage and mitigate threats effectively. These tools not only help with detecting and analyzing incidents but also ensure that a coordinated response is carried out to resolve security issues quickly. From automation to reporting and collaboration, these tools support every stage of the incident response process.
Let’s dive into the key features that make these tools essential for a comprehensive security strategy.
Endpoint detection and response (EDR) tools are critical in protecting devices that connect to your network. These tools are designed to monitor, detect, and respond to potential security threats at the endpoint level. Given the rise of remote work and the growing number of connected devices, securing endpoints has become a primary concern. EDR tools can detect malicious activity, prevent further damage, and even automate remediation to neutralize threats quickly.
In this section, we will explore the role of EDR tools in cybersecurity and how they work in conjunction with extended detection and response (XDR).
EDR tools monitor endpoint activity for abnormal behavior, which could indicate a security breach. They track processes, files, and network connections to detect suspicious activity. By continuously monitoring endpoints, these tools can quickly identify and stop malware, ransomware, or unauthorized access attempts before they spread to other parts of the network. EDR tools provide real-time visibility into endpoints and offer detailed forensic data to investigate incidents thoroughly.
XDR enhances EDR by providing a more comprehensive view of the entire IT ecosystem. XDR tools extend the detection and response capabilities beyond endpoints to include servers, networks, and other systems. By aggregating data from across the organization, XDR allows for a more coordinated and effective response to security incidents. These tools use machine learning and behavioral analytics to detect complex, multi-stage attacks that traditional EDR systems might miss.
SIEM systems play a pivotal role in cybersecurity by providing centralized monitoring and analysis of security events across an organization. By collecting log data from various sources, SIEM tools enable security teams to gain comprehensive insights into network activity, detect anomalies, and respond to threats in real time. These systems improve incident detection and support compliance and auditing efforts by providing detailed event logs. In this section, we will explore the functionalities of SIEM systems and how they contribute to an organization's security posture.
SIEM systems provide real-time analysis of security events by aggregating and normalizing data from multiple security tools. They help security teams identify threats as soon as they arise, providing visibility into network activities. Real-time alerts ensure that incidents are addressed immediately, minimizing potential damage.
SIEM systems normalize log data from various sources into a standardized format, making it easier to detect patterns and correlations. This enables security teams to identify incidents quickly by comparing logs from different systems. Normalization also aids in providing context around the events, making it easier to understand the scope and impact of a potential attack.
SIEM systems come equipped with robust reporting and alerting capabilities, allowing security teams to receive timely notifications of suspicious activities. These alerts are highly customizable, ensuring that critical threats are prioritized. SIEM tools also provide detailed reports that assist in compliance audits and incident investigations.
Vulnerability scanners are essential for identifying weaknesses in an organization's network, systems, and applications. By continuously scanning for known vulnerabilities, these tools help organizations stay ahead of potential threats and ensure that security gaps are closed before attackers can exploit them. Vulnerability scanners also play a critical role in patch management, guiding organizations on which vulnerabilities to address first.
In this section, we will discuss how vulnerability scanners work and their importance in a comprehensive incident response strategy.
Vulnerability scanners are designed to detect security flaws within networks, systems, and applications. These tools automatically search for unpatched software, configuration weaknesses, or misconfigurations that attackers could exploit. By identifying these vulnerabilities early, organizations can prevent attacks and reduce the overall risk of a breach.
Once vulnerabilities are identified, scanners typically assign a risk rating based on severity, helping security teams prioritize remediation efforts. Addressing high-priority vulnerabilities first reduces the attack surface and minimizes the likelihood of a successful attack. Vulnerability scanners also provide detailed reports that outline specific remediation steps, making it easier to address each issue.
Intrusion Detection and Prevention Systems (IDPS) are designed to monitor network traffic for malicious activities and automatically block potential threats. These systems analyze network traffic in real time to detect attacks such as unauthorized access attempts, malware, and denial-of-service attacks. IDPS systems are an essential part of a layered security strategy, providing both detection and prevention capabilities to defend against evolving cyber threats.
In this section, we will explore the features of IDPS systems and their role in incident response.
IDPS tools monitor network traffic for suspicious patterns that could indicate a security threat. By analyzing inbound and outbound traffic, IDPS can detect a wide range of attacks, including malware infections, network intrusions, and other malicious activities. Once a potential threat is detected, the system can immediately alert security teams and take automated actions to block the threat.
A key advantage of IDPS systems is their ability to automatically respond to detected threats. Once a threat is identified, the system can take predefined actions such as blocking malicious IP addresses, isolating compromised devices, or stopping malicious processes. This automated response helps prevent further damage and reduces the time attackers have to exploit vulnerabilities.
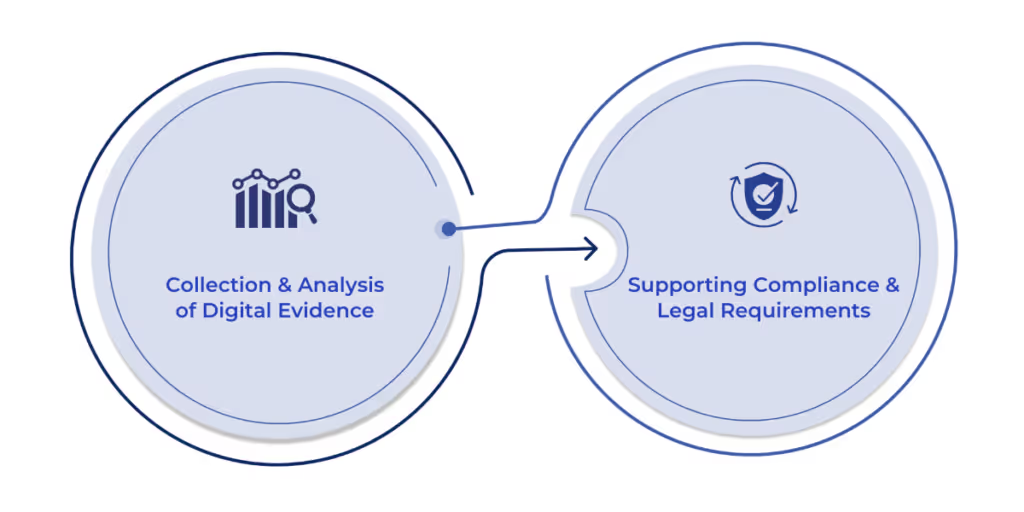
Digital forensics tools are essential for collecting, preserving, and analyzing digital evidence following a security incident. These tools provide investigators with the data needed to determine the cause and scope of a breach. By supporting the collection of evidence, digital forensics tools ensure that organizations comply with legal and regulatory requirements, making them an integral part of the incident response process.
In this section, we will examine the role of digital forensics tools in incident investigations.
Digital forensics tools enable the systematic collection and analysis of evidence from compromised systems. These tools can capture and analyze disk images, memory dumps, logs, and network traffic to reconstruct the events leading up to a security incident. This information is critical for identifying how the attack occurred and determining the full extent of the damage.
Digital forensics tools also play a key role in ensuring compliance with legal and regulatory requirements. In many industries, there are strict regulations regarding the handling of digital evidence, including chain-of-custody protocols and data preservation rules. Forensic tools ensure that evidence is collected and preserved in a forensically sound manner, supporting legal proceedings and ensuring compliance during investigations.
Incident response tools are vital for maintaining a strong security posture in today’s cyber threat landscape. By leveraging a combination of endpoint security, SIEM, vulnerability scanners, IDPS, and digital forensics tools, organizations can quickly detect, respond to, and recover from security incidents. Integrating automation, threat intelligence, and cloud-based tools further enhances the capabilities of these tools, ensuring that organizations can stay ahead of evolving threats.
At WaferWire, we understand the challenges organizations face in securing their systems against sophisticated cyber threats. Our team of experts is ready to help you implement the most effective incident response tools tailored to your unique needs. Whether you're looking to enhance detection capabilities, automate responses, or integrate threat intelligence, we’re here to provide the guidance and support you need.
Reach out to WaferWire today to secure your infrastructure, streamline your incident response, and ensure your organization is prepared for the future of cybersecurity. Let's build a stronger, safer security posture together.

