
Understanding Infrastructure as Code (IaC) Security and Best Practices
Murthy S
2025-01-30

Talk to our cloud experts
Subject tags
According to a MarketsandMarkets report, the global Infrastructure as Code (IaC) market was worth $0.8 billion in 2022 and is expected to grow to $2.3 billion by 2027. This represents an annual growth rate of 24.0% during this period. While the benefits of IaC are evident, the security implications are frequently neglected.
As organizations depend more on automated processes, robust IaC cybersecurity is crucial. IaC simplifies compliance and auditing and allows for the integration of strong security policies directly into the infrastructure.
In this article, you will learn what IaC security is, why it is important, the risks involved, and IaC security best practices for keeping your infrastructure safe.
What is IaC Security?
Infrastructure as Code security refers to the methodologies, tools, and practices aimed at securing the code and processes used to define, provision, and manage infrastructure. Unlike traditional IT setups, where infrastructure is configured manually, IaC relies on declarative or procedural code stored in version-controlled repositories.
While this approach improves automation and scalability, it also means that vulnerabilities, misconfigurations, or malicious changes in the code can directly impact the deployed infrastructure. Understanding what IaC security entails provides a solid base for exploring how it works in practice, which involves a combination of tools, processes, and proactive measures.
How does IaC Security Work?
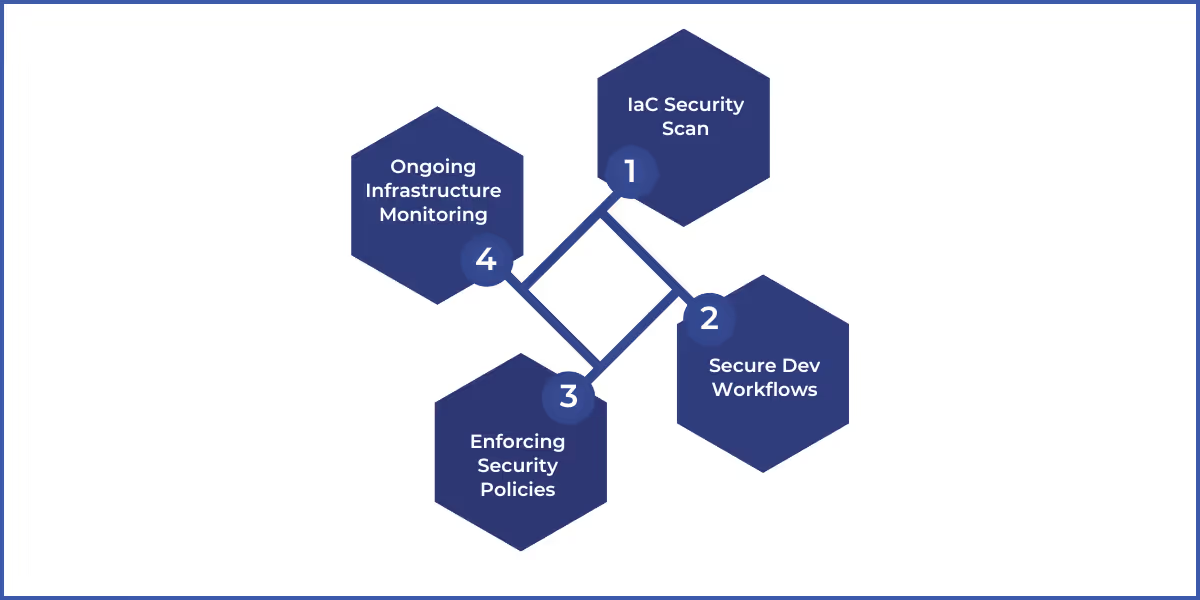
Infrastructure as Code (IaC) security involves keeping your cloud infrastructure safe while managing it through code. Here’s how it operates:
1) Automated Scanning for IaC Vulnerabilities
IaC security tools automatically detect issues like insecure access controls, misconfigured cloud services, or excessive permissions that violate least privilege principles. Static code analysis, a core feature, reviews IaC scripts against established security policies and best practices without executing the code. This ensures safe configurations before deployment.
2) Embedding Security in Development Workflows
Incorporating security checks early in the development cycle—using a “shift-left” strategy—allows developers to identify and fix vulnerabilities before code goes live, reducing security risks
3) Enforcing Security Policies
A centralized policy engine ensures IaC templates adhere to standards like NIST guidelines or custom organizational policies. Non-compliant templates are flagged or blocked to prevent insecure deployments.
4) Ongoing Infrastructure Monitoring
Once the infrastructure is deployed, monitoring tools continuously assess changes, identifying configuration drift or deviations from the intended setup. This proactive approach helps maintain long-term security and compliance.
By understanding how these components work together, we can appreciate the comprehensive nature of IaC security and its role in safeguarding modern infrastructure.
Why is IaC Security Important?
Cybersecurity flaws in your IaC configurations can expose misconfigured cloud services, unsecured APIs, or open ports to exploitation. For example, AWS S3 buckets in CloudFormation templates with incorrect permissions could unintentionally grant public access to sensitive data.
This highlights the critical need for IaC security in cloud environments. By integrating security controls directly into infrastructure definitions, you can conduct automated compliance checks—such as against CIS benchmarks or NIST guidelines—during CI/CD pipelines. Identifying and addressing vulnerabilities early in development prevents risks from escalating to production.
Recognizing the importance of IaC security naturally leads to the next question: what tangible benefits does it provide?
Benefits of IaC Security
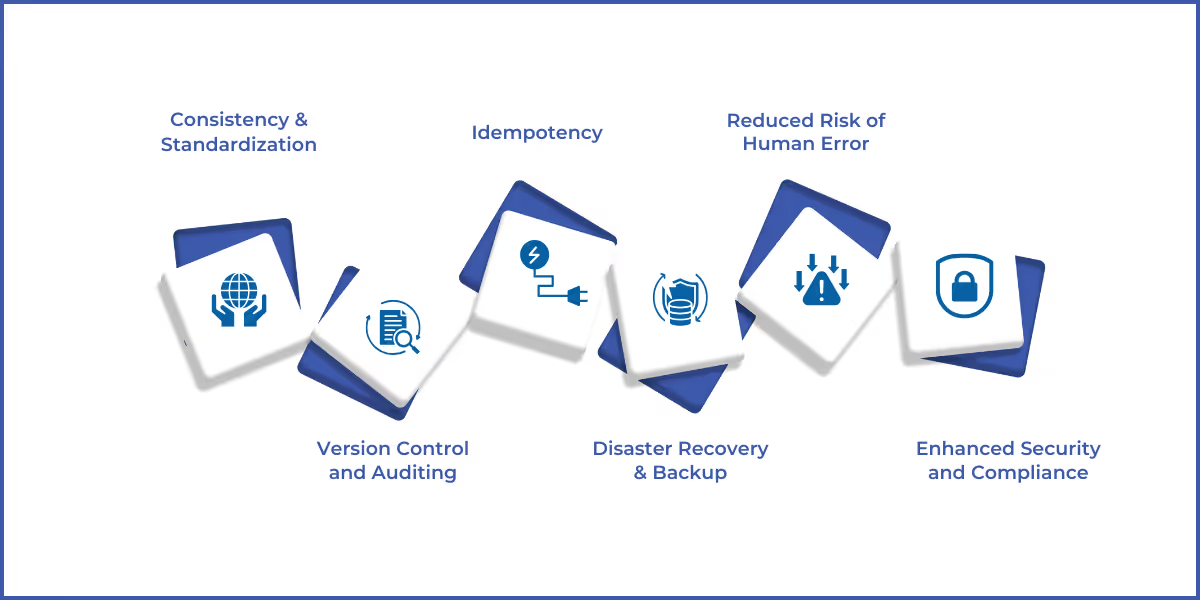
Beyond mitigating risks, IaC security offers operational consistency, enhanced compliance, and strategic benefits that align with business goals. Let’s explore these benefits in detail.
1. Consistency and Standardization
IaC ensures that infrastructure configurations are consistent across environments, eliminating discrepancies caused by manual setup. For instance, a production environment configured through IaC is identical to its staging counterpart, reducing unforeseen errors during deployment. Security policies embedded in IaC templates also ensure compliance from the outset, minimizing the risk of deviations.
2. Version Control and Auditing
IaC files stored in repositories provide a detailed audit trail. This ensures that every change is logged, reviewed, and traceable. If a security incident occurs due to a misconfiguration, version control allows teams to pinpoint the specific change responsibly and revert to a secure state. This traceability also facilitates compliance reporting.
3. Idempotency
IaC enables idempotent operations, ensuring that infrastructure configurations remain predictable, even after repeated deployments. This reduces the risk of accidental changes introducing vulnerabilities. For example, reapplying an IaC template won’t duplicate resources or open unintended network ports, maintaining stability and security.
4. Disaster Recovery and Backup
IaC configurations act as blueprints for your infrastructure. In the event of a failure or disaster, resources can be redeployed quickly and securely using predefined templates. This capability significantly reduces downtime, protects critical business operations, and ensures rapid recovery.
5. Reduced Risk of Human Error
Automation minimizes human involvement in provisioning, reducing the likelihood of errors such as misconfigured access controls or open ports. By automating repetitive tasks, IaC allows teams to focus on higher-value activities while ensuring infrastructure is provisioned securely.
6. Enhanced Security and Compliance
IaC workflows can incorporate predefined security policies and compliance checks, ensuring that every deployed resource adheres to organizational and regulatory standards. For instance, IaC templates can enforce encryption for all databases or restrict public access to sensitive resources by default, creating a secure baseline.
To fully realize these benefits, leveraging the right tools becomes critical. These tools not only automate security tasks but also ensure compliance with organizational policies. Here’s a look at the tools that enable IaC security.
Infrastructure as Code (IaC) Security Tools
The following tools are widely recognized for their ability to identify vulnerabilities and enforce security policies:
- TFSec: A static analysis tool that scans Terraform templates for security issues, including misconfigurations and policy violations.
- Jit: A security-as-code platform that integrates directly into CI/CD pipelines to detect and mitigate IaC risks. Its real-time feedback empowers developers to fix issues before deployment.
- Checkov: A policy-as-code framework for scanning Terraform, Kubernetes, and CloudFormation templates. It provides in-depth reports and remediation steps.
- Prowler: A multi-cloud security scanner focusing on AWS, identifying security gaps and compliance violations.
- Conftest: A tool for testing configuration files against custom policies written in Rego (OPA). It’s highly customizable and ideal for advanced use cases.
Each tool plays a specific role in building a comprehensive IaC security strategy, providing organizations with the resources needed to secure their infrastructure effectively.
Real-World Applications of IaC Security
While tools and strategies are essential, the real value of IaC security lies in its practical applications. Organizations across industries are leveraging IaC security to achieve measurable outcomes:
1. Finance and Banking
The financial sector relies heavily on IaC security to safeguard sensitive customer and transactional data. By automating the deployment of secure configurations for servers, databases, and networks, banks and financial institutions ensure compliance with strict regulatory standards like PCI DSS and SOX.
2. Healthcare
In healthcare, IaC security plays a crucial role in protecting patient data and maintaining regulatory compliance. By embedding security policies directly into IaC templates, healthcare providers can ensure that systems handling sensitive medical records meet standards such as HIPAA and GDPR.
3. Technology and SaaS Companies
Technology firms and SaaS providers integrate IaC security into their CI/CD pipelines to ensure that infrastructure and applications are secure from the ground up. This approach helps developers identify misconfigurations and vulnerabilities early in the development lifecycle, reducing the risk of deploying insecure environments.
These applications highlight the tangible impact of IaC security on operational efficiency and real-world utilization. Despite its numerous applications, IaC introduces challenges that organizations must address to ensure robust security.
IaC Security Challenges and Risks
While automation brings efficiency, scalability, and reliability, it also introduces a set of security concerns that require careful management.
Configuration Errors and Drift
A single error in an IaC template can trigger a chain reaction. For example, an AWS CloudFormation template might accidentally configure a security group to allow public access, exposing critical databases. Additionally, configuration drift—caused by manual changes or undocumented adjustments—can lead to vulnerabilities over time, as the actual infrastructure diverges from its intended state.
Forgotten or Orphaned Resources
Also known as ghost resources, these include untagged or abandoned components like unused virtual machines or storage volumes. Consider a marketing agency using Azure Resource Manager without enforcing proper tagging policies. Over time, these forgotten resources can accumulate, inflating costs and increasing the attack surface. Implementing consistent resource tagging can mitigate this risk.
Poor Secret Management
Storing credentials, API keys, or other sensitive data in plaintext or unsecured files can lead to privilege escalation attacks. For instance, an e-commerce platform using Ansible might save API secrets in plaintext configuration files, leaving them vulnerable if exposed. Securely managing secrets is vital to reducing this risk.
Over-Privileged Access
Granting users unnecessary permissions—whether by mistake or default—significantly increases the attack surface. To counter this, organizations should adopt the Principle of Least Privilege (PoLP), ensuring that every user or service has access only to the minimum permissions necessary for their role.
To overcome these challenges and maximize the effectiveness of IaC security, organizations should adopt proven best practices. These practices form the cornerstone of a robust security strategy.
IaC Security Best Practices.
Securing Infrastructure as Code (IaC) is key to preventing misconfigurations and ensuring compliance in cloud environments. Here are some best practices to enhance security and build resilient infrastructure.
Adopt a Shift-Left Approach
Incorporate security checks early in the development lifecycle to identify issues before deployment. For instance, integrating static code analysis in the pre-commit stage can catch misconfigurations before they reach production.
Use Version Control Systems
Store IaC configurations in repositories with strict access controls and commit-level auditing. This not only enhances security but also enables collaborative development.
Automate Security Testing
Integrate tools like TFSec and Checkov into CI/CD pipelines for continuous scanning. Automated testing ensures that vulnerabilities are identified and addressed consistently.
Define Policies as Code
Use frameworks like Open Policy Agent to enforce rules for resource configurations. Policy as Code ensures consistent enforcement of security standards across environments.
Implement Least Privilege Access
Ensure resources and identities follow the principle of least privilege to minimize attack surfaces. For example, restricting admin access to essential personnel can reduce the risk of insider threats.
Monitor and Audit Deployed Resources
Use runtime monitoring to detect configuration drift and unauthorized changes. Continuous auditing helps maintain alignment with security policies.
Educate and Train Teams
Conduct regular training sessions on IaC security tools and practices to build organizational expertise. Teams that understand security risks and tools are better equipped to mitigate them.
Conclusion
Infrastructure as Code (IaC) security plays a vital role in modern infrastructure management by balancing the efficiency and scalability of automation with the need for robust safety measures. Integrating security into the IaC lifecycle allows organizations to proactively tackle vulnerabilities, ensure compliance, and build a resilient infrastructure. Applying consistent security policies across environments minimizes human errors and strengthens overall protection.
Embracing best practices—such as automated scanning, shift-left security, and least privilege access—is key to creating a secure IaC environment. As IaC evolves, focusing on security will empower organizations to innovate with confidence while keeping their critical assets protected.
Looking to automate, scale, and optimize your IT infrastructure? WaferWire offers customized Infrastructure as Code (IaC) strategies that align with your business goals, helping you:
- Accelerate Deployments: Achieve faster, more reliable software releases with automated infrastructure.
- Simplify Management: Automate provisioning and reduce manual effort to enhance operational efficiency.
- Ensure Consistency and Scalability: Standardize your infrastructure across environments for improved reliability and growth.
Take control of your infrastructure with automation-driven solutions that enhance agility and performance.Get Started Today to discover how our IaC solutions can streamline your operations and future-proof your business!
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)












