
Guide to Security Roles in D365 Finance & Operations
Murthy S
2025-07-14

Talk to our cloud experts
Subject tags
Security roles in Dynamics 365 Finance and Operations are a fundamental part of maintaining control over who can access, modify, or interact with specific areas of the system. With multiple departments relying on sensitive financial, operational, and HR data, it becomes essential to assign access based on clearly defined responsibilities. The platform’s role-based security model allows administrators to enforce data integrity and ensure that users perform only the actions relevant to their job functions.
Understanding how security roles work is critical for effective governance and regulatory compliance. This guide explains how Dynamics 365 Finance and Operations structures security roles, relates them to duties and privileges, and enables organizations to manage them to safeguard data and optimize operational efficiency
What Are Security Roles in Dynamics 365 Finance and Operations?
Security roles in Dynamics 365 Finance and Operations act as access blueprints that govern what users can do within the system. Rather than assigning permissions directly to individuals, the platform groups tasks and permissions into roles that align with job responsibilities, ensuring consistency and ease of management.
These roles are designed to support business processes while protecting sensitive data. By mapping access to actual work functions, organizations can enforce internal controls, minimize human error, and meet regulatory compliance—all while ensuring users have the tools they need to perform their jobs effectively.
Key Components of the Security Model in Dynamics 365

The security model in Dynamics 365 Finance and Operations is built on a layered structure that ensures controlled, scalable access. At its core, the model consists of roles, duties, and privileges, each playing a distinct role in defining what a user can do in the system.
Here are the components of the security model:
- Roles: Roles represent a user’s business function, such as “Accounts Payable Clerk” or “Warehouse Manager.” They act as containers for duties and privileges and are the top layer in the security model. Assigning roles to users grants them access to related functionality.
- Duties: Duties are collections of related tasks that represent a part of a business process. For example, the “Maintain Vendor Payments” duty might include privileges for entering payment journal lines, validating them, and posting.
- Privileges: Privileges are the most granular level of control and represent individual system actions, such as “Edit vendor record” or “Post general journal.” They are combined into duties and indirectly assigned to roles.
- Security roles in Dynamics 365 follow a hierarchical model in which the system inherits permissions through the structure, such as:
- Roles inherit permissions from duties, and duties inherit permissions from privileges.
- Security roles do not directly grant access; rather, access is derived from the duties and privileges assigned to them.
- When customizing or extending roles, child elements (duties/privileges) retain inherited access unless explicitly modified.
- Hierarchical access also applies to organizational structures, such as legal entities and operating units. A user may have access to specific entities depending on how their role is scoped.
This layered model enables organizations to manage access at a granular level, ensuring that users have appropriate permissions without exposing sensitive or unrelated data. To implement this effectively, it’s essential to understand the different types of security roles available in Dynamics 365 Finance and Operations and how they support various business functions.
Also Read: How to Set Up Power BI with Dynamics 365 for Finance and Operations
Types of Security Roles in Dynamics 365 Finance and Operations
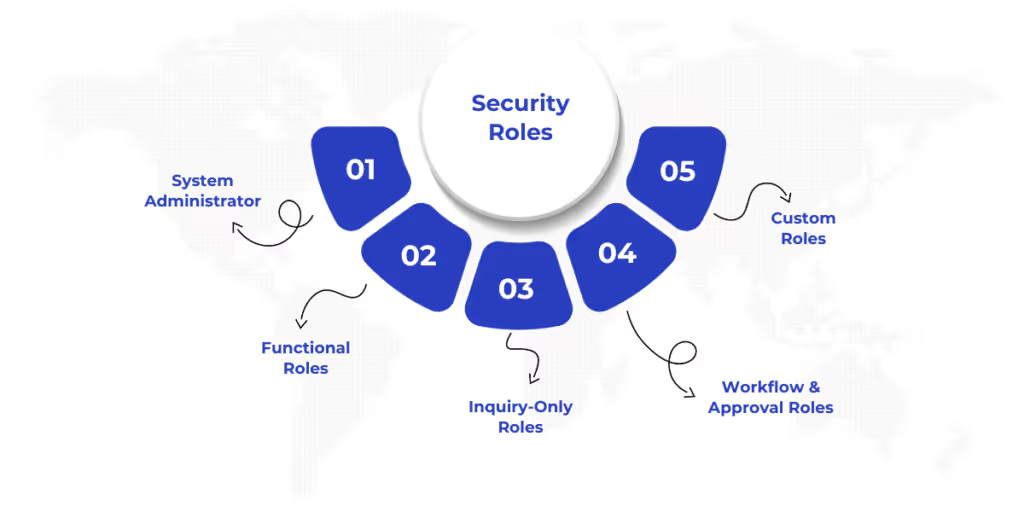
Dynamics 365 F&O uses a Role-Based Access Control (RBAC) model. It offers a wide range of role-based security to suit different organizational needs, from system-wide administration to task-specific responsibilities. These roles are designed to optimize user access by aligning them with business functions.
Here are the main types of security roles commonly used:
1. System Administrator
This is the highest-level role with full access to all modules, data, and configurations across the environment. Users with this role can create, assign, or modify other roles and manage the entire security structure.
2. Functional Roles
These roles are assigned based on specific job functions, such as Accounts Payable Clerk, Procurement Manager, or General Ledger Accountant. They allow access to the relevant parts of the system required for day-to-day operations, including posting transactions, approving documents, or managing vendor information.
3. Inquiry-Only Roles
These roles are tailored for users who need to view data without making changes. For example, a finance reviewer or an internal auditor may require access to reports or transaction histories but not have permission to create or modify records.
4. Workflow and Approval Roles
These roles are associated with approval hierarchies and workflow participation. They allow users to review and approve documents such as purchase requisitions, journal entries, or expense reports, depending on their authority within the organization.
5. Custom Roles
Organizations can create custom roles to reflect specific operational structures or compliance requirements. Custom roles are built by combining duties and privileges tailored to support specialized processes or internal control needs.
Each of these roles can be further refined through duties and privileges to ensure users have the exact access they need.
How to Assign Security Roles in Dynamics 365 Finance and Operations
Assigning roles is the foundation of user access control in Microsoft Dynamics 365 Finance and Operations. Each user must receive one or more security roles that reflect their job responsibilities. Assigning roles is a straightforward process, but administrators should handle it carefully to ensure users have appropriate access.
Here are the steps to assign security roles:
- Go to System Administration > Users > Users to access the list of active user accounts.
- Click on the user’s name to open their profile.
- Select Assign Roles from the top menu. You’ll see a list of all available roles in the system.
- Choose the appropriate roles. You can assign multiple roles if needed.
- After you select the roles, click OK to finalize the assignment.
- Test the Role Assignment.
Update roles when users shift departments, take on new responsibilities, or when new processes are introduced. Regular access reviews, especially during audits, ensure that permissions remain aligned with actual job duties.
Once roles are assigned, managing them effectively is key to maintaining long-term security and compliance.
How to Manage Security Roles in Dynamics 365 F&O
Managing security roles is an ongoing responsibility. As business structures evolve, so do user responsibilities, systems, and compliance requirements. Poorly managed roles can lead to permission creep or data exposure.
Here’s how you can effectively manage and maintain a streamlined security structure:
1. Enforce Segregation of Duties (SoD)
SoD is a critical control mechanism that reduces the risk of fraud and errors. The goal is to ensure that no single user can complete high-risk transactions end-to-end, like initiating and approving vendor payments.
Here’s how you can implement SoD:
- Ensure that roles clearly separate functions like data entry, review, and approval.
- Use SoD rules in D365 to automatically detect role combinations that could create conflicts.
- Periodically audit user roles to identify and remediate SoD violations.
- In cases where overlapping roles are necessary, log the exception and monitor the user’s activity closely.
SoD helps enforce proper internal controls, but overlapping roles may still exist. Managing these conflicts is the next step.
2. Identify and Resolve Role Conflicts and Overlaps
Over time, users may accumulate multiple roles as their responsibilities evolve. Without proper oversight, this can result in unintended or excessive access. These overlaps not only pose a security risk but also complicate compliance.
Here’s how to handle role conflicts:
- Run security diagnostics
- Leverage the SoD conflict report to detect and resolve conflicts
- Evaluate redundant or overlapping roles and consolidate them wherever possible.
- Set up approval workflow for role changes.
- Audit Role Changes
With a solid process for assigning and managing roles, you establish a foundation for secure and efficient operations. Managing security roles effectively requires the right set of tools.
Suggested Read: Understanding Dynamics 365 for Finance & Operations
Tools for Configuring and Diagnosing Security Roles
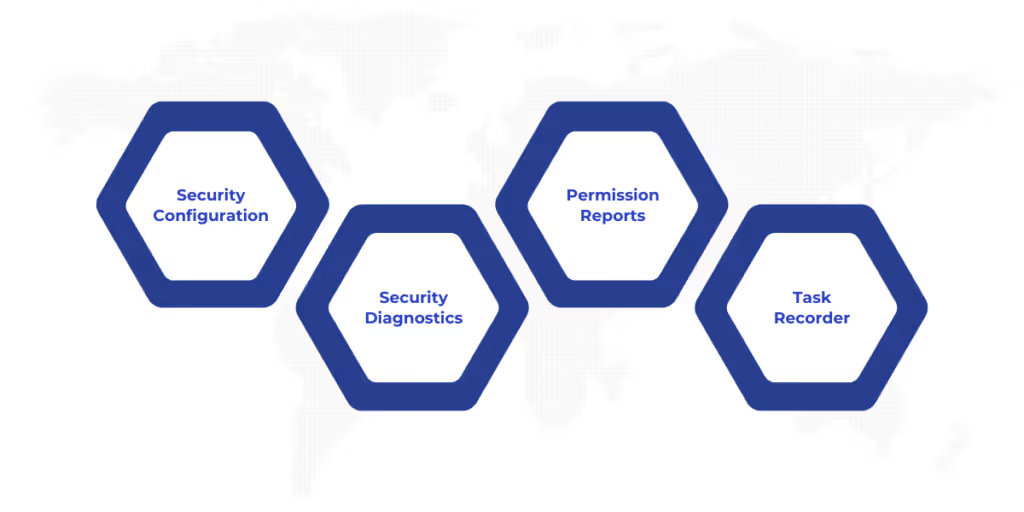
Dynamics 365 Finance and Operations offers a suite of integrated tools designed to support the secure and efficient management of user roles. These tools help administrators configure roles, analyze security structures, and identify potential risks or access issues.
Here are some of the key tools that use to configure and diagnose security roles.
- Security Configuration: Accessed via System Administration, this tool allows you to create, edit, and view roles, duties, and privileges in a structured hierarchy.
- Security Diagnostics: Helps identify missing permissions when users encounter access errors, making it easier to adjust role assignments accurately.
- Permission Reports: Useful for auditing and reviewing the specific access a role, duty, or privilege grants across the system.
- Task Recorder: Supports role design by mapping out the steps of a business process and identifying the required security access.
With the right tools in place, configuring and maintaining security roles becomes more efficient and reliable. However, effective security management also depends on how thoughtfully designers create and implement those roles. Let’s explore some tips next.
Tips for Designing Effective Security Roles
Designing security roles in Dynamics 365 Finance and Operations requires more than simply assigning permissions. It demands thoughtful planning to align system access with real-world responsibilities, ensure regulatory compliance, and protect sensitive business data.
Here are the key tips to build security roles that are both effective and scalable:
- Align Roles with Business Processes: Base roles on actual job functions and workflows to ensure access reflects real responsibilities, not just department labels.
- Reuse Duties and Privileges: Utilize existing duties and privileges where possible to maintain consistency, reduce errors, and ease future updates.
- Apply the Least Privilege Principle: Grant users only the minimum access needed for their tasks to minimize security risks and unauthorized data exposure.
- Use Role-Based Access Control (RBAC): Assign roles to user groups instead of individuals for better scalability, consistency, and easier management.
- Maintain Role Documentation: Document each role's purpose, permissions, and usage clearly to support audits, troubleshooting, and onboarding.
- Test Roles Before Deployment: Validate roles in a sandbox to ensure they function as intended and don’t disrupt workflows or grant excess access.
- Monitor and Refine Roles: Regularly review role usage through logs and reports to identify unnecessary access or outdated permissions.
Conclusion
Implementing and managing security roles in Dynamics 365 Finance and Operations is essential for safeguarding sensitive data, ensuring regulatory compliance, and enabling efficient user access across business functions. A well-defined security structure, built on roles, duties, and privileges, helps organizations maintain control without compromising productivity.
WaferWire supports businesses in creating and optimizing security roles tailored to their specific operational and compliance needs. Our team helps ensure that your security model is designed to minimize risk and is scalable as your organization grows. Whether you are starting fresh or refining your current setup, we provide expert guidance every step of the way.
Need help building a secure role-based model in Dynamics 365 Finance and Operations? Schedule a consultation to explore tailored solutions for your organization.
FAQs
Q1. What are security roles in Dynamics 365 Finance and Operations?
A. Security roles define a user's access within the system based on their job responsibilities. They group related duties and privileges to ensure appropriate access while supporting internal controls.
Q2. How do duties and privileges relate to security roles?
A. Duties group tasks related to a business process, while privileges grant the lowest level of access to perform specific actions. Roles include duties, which in turn include privileges, forming a layered access structure.
Q3. Can I customize security roles in Dynamics 365 F&O?
A. Yes, you can modify existing roles or create new ones to fit your organization’s needs. Custom roles help align security with internal policies, compliance requirements, or unique business processes.
Q4. How can I detect role conflicts or segregation of duties issues?
A. Dynamics 365 offers tools like the Segregation of Duties (SoD) rule editor and security diagnostics. These help identify and resolve conflicts where users may have excessive or risky combinations of access.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)












